Overview
Northrop Grumman is committed to ensuring that capable businesses of all types receive meaningful subcontracting opportunities with Northrop Grumman. To begin the process, please follow the steps outlined below. Potential suppliers (Small or Large) should utilize the Small Business Liaison Officers (SBLO) as their initial point of contact at Northrop Grumman.
Getting Started
If you are interested in doing business with Northrop Grumman, please read the recommended steps below.
New Supplier Registration Process through the Ariba Network
Northrop Grumman has partnered with SAP Ariba to manage our Supplier registration and on-boarding process using SAP Ariba Network. All steps below must be completed to become a Northrop Grumman supplier.
Northrop Grumman Supplier Registration Guide
This guide provides detailed instructions for completing Steps 1-4, and for ongoing use of your Ariba Network supplier account to update your information for Northrop Grumman.
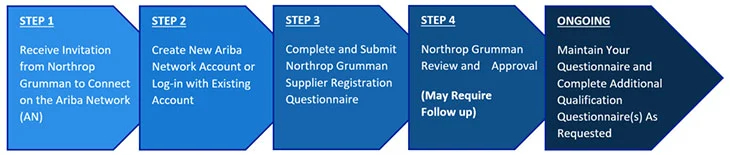
- Receive Invitation from Northrop Grumman to Connect on the Ariba Network (AN)
- Create New Ariba Network Account or Log-in with Existing Account
- Complete and Submit Registration Questionnaire
- Northrop Grumman Review and Approval (May Require Follow Up)
- Maintain Your Questionnaire and Complete Additional Qualification Questionnaire As Requested
Note: Registering for an Ariba Network account does not mean you are registered as a supplier with Northrop Grumman. You will need to complete Northrop Grumman’s Registration Questionnaire and it will need to be approved before you are considered registered with Northrop Grumman.
Anti-Human Trafficking Compliance
Northrop Grumman fully supports the elimination of human trafficking and slavery, including from the supply chain. We do not tolerate trafficking in persons, including the procurement of commercial sex acts, and the use of forced or child labor. We have implemented comprehensive policies and procedures, including our Standards of Business Conduct for Suppliers and Other Trading Partners, which require our employees and suppliers to comply with applicable law, including but not limited to requirements under the Federal Acquisition Regulation (FAR) and/or UK Modern Slavery Act, and behave in an ethical manner.
Cybersecurity Resources for Suppliers
As government, prime contractors, and suppliers are increasingly targeted by cyber attacks, companies and their suppliers must work together to protect sensitive information and intellectual property. Awareness of cyber risks and implementation of effective cybersecurity controls and defenses is vital. For timely information about current security issues, vulnerabilities, and exploits, please consult the CISA website.
Northrop Grumman understands the important role our suppliers play in protecting our and our customers’ information and networks from cyber threats. We also understand the value that cybersecurity maturity plays in achieving and maintaining a competitive advantage for our company and our suppliers. Our mutual success is impacted by our ability to both identify and effectively manage cyber risks. Building a cybersecurity posture capable of mitigating risk is essential. Northrop Grumman recognizes that our suppliers must also develop and maintain their own cybersecurity postures. We invite you to view this short video developed through a partnership between the Northrop Grumman Global Supply Chain and Information Security organizations. The video provides recommendations and resources related to some of the biggest cybersecurity challenges including spear phishing schemes, business email compromise and ransomware attacks.
Northrop Grumman has collaborated with other Defense Industrial Base (DIB) companies to establish theCyberAssist Website. This website will assist suppliers in enhancing their cyber security protections by identifying and posting links to helpful publicly available cybersecurity resources. The resources were selected both to help companies (i) meet DoD and other U.S. cybersecurity standards applicable to U.S. federal contractors (e.g., FAR Basic Safeguarding clause, DFARS Safeguarding Covered Defense Information (CDI) clause, DoD Cybersecurity Maturity Model Certification (CMMC)); and (ii) otherwise improve their current cybersecurity protections.
Another helpful resource is CI2 Project Spectrum (DoD Small Business Office Sponsored). Part of the Cyber Integrity Initiative (CI2) – and supported by the Department of Defense’s (DoD) Office of Small Business Programs (OSBP), Project Spectrum provides resources, information, training, and risk assessments to help companies and institutions improve cyber readiness and comply with DoD requirements. Suppliers to Northrop Grumman need to comply with our standard terms and conditions.
If you have any comments or questions regarding the provided supplier resources, please click here.
Secure Access
Protected applications on OASIS require additional authentication.
Global Trade Security (CTPAT)
Northrop Grumman has been a proud and supportive member of Customs Trade Partnership Against Terrorism (CTPAT) since 2005. Implemented in November 2001 by U.S. Customs and Border Protection under the Department of Homeland Security, CTPAT is a collaborative network of government and industry partners with a common goal to ensure a compliant, lawful, and secure global trade ecosystem.
As a company with global operations and a dedication to protecting its people, assets, and information; Northrop Grumman actively promotes a culture of security among its employees, contractors, visitors, and suppliers. By adhering to the CTPAT Minimum Security Criteria, Northrop Grumman further commits to being a trusted trading partner.
Suppliers and Logistics Service Providers
Recognizing supply chain security as a global responsibility, Northrop Grumman encourages integration of enhanced security measures at every link in the supply chain, from production to transport to final delivery. We encourage our global business partners to integrate and maintain a multi-layered security approach to facilities, procedures, and practices. Additionally, Northrop Grumman recommends participation in CTPAT or a relevant Authorized Economic Operator (AEO) program.
Statement of Support
Global trade security is a collective effort. Ensuring a safe, legitimate, and compliant supply chain mutually benefits all stakeholders. By participating in CTPAT, and prioritizing the Minimum-Security Criteria, Northrop Grumman commits to fulfilling its role in this critical risk-mitigation program.
Sarah H. Corkran
Corporate Vice President, Enterprise Global Supply Chain
Quick Links
